Lots of useful feedback in here so far.
I've decided to begin with an extremely conservative strategy: the bleeding-edge source revision of Decker now includes an interface named "danger", which is normally not accessible. If you tweak the makefile to define the symbol "DANGER_ZONE" and build native-Decker from scratch, you can use this interface to do most of the things Lilt could do previously:
- raw file I/O
- filesystem traversal
- access environment variables
- and (if you're on a Unixy operating system) invoke shell commands(!)
Obviously there's a whole host of possible foot-guns, sharp corners, inconsistent cross-platform behaviors, etc, but also it's possible to do a few pretty neat things like grab live data from the internet:
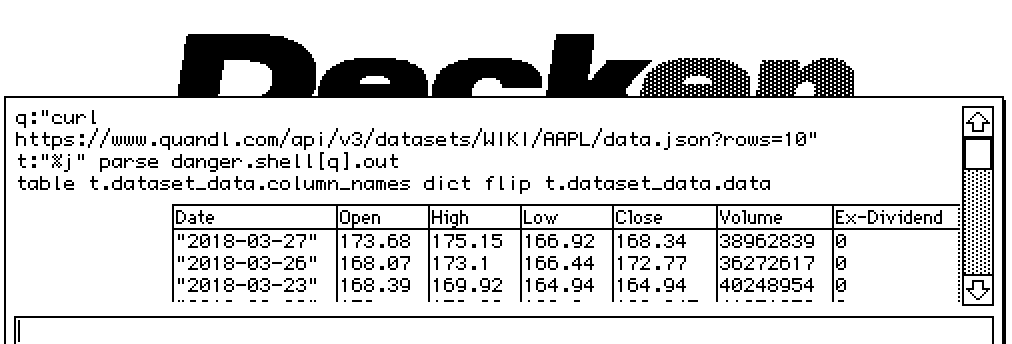
For the time being, I intend to leave The Danger Zone disabled in official binary releases; if you can build Decker from source, I think it's a reasonable assumption that you understand the associated risks. Depending on how people use this functionality, I'll consider offering some other mechanism(s) for opting into danger.
Thoughts?

