Decker comes in two flavors: web-decker (which runs in web browsers) and native-decker (which is a native executable for MacOS, Windows, Linux, BSD, etc).
Since Decker's initial release, I've tried to maintain parity between these implementations wherever possible. As a result, they both limit themselves to fairly strict sandboxing constraints inherited from web browsers. For example, Decker can open files on your local computer, but only through a manual file-picker dialog. A nice side effect of this approach is that it upholds a principle of informed consent: Decks cannot do nasty or invasive things like rummage through your documents or phone home with telemetry without the user's awareness.
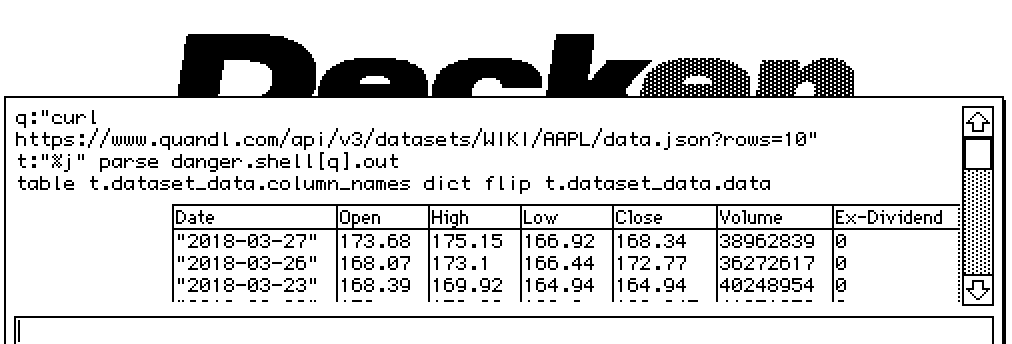
I have heard a number of Decker users (and, more tenuously, prospective users) state that they would be interested in using Decker for a wider range of things if they could write programs that are less tightly sandboxed. Filesystem I/O and traversal and network access are frequent asks. If a user installs Python and runs a script on their computer, it's completely normal for that script to be able to monkey around at will with the user's files, and web-decker already provides a robust means of isolating decks you don't entirely trust. Perhaps the cautious approach is simply inconvenient?
I would very much like to hear your opinions on this matter!
- Should native-decker have APIs for doing potentially hazardous or invasive things to the local computer, and if so what is the minimum functionality Decker should expose?
- Should native-decker prompt for informed consent when using these APIs, or is this approach needlessly cautious and annoying?
- What, specifically, would you like to build if you had access to the things you describe?