Heya, we've got someone complaining that their browser wanted to update to play our unity webgl build.
We've tried to replicate this. After a bunch of reloads, we got this very weird message: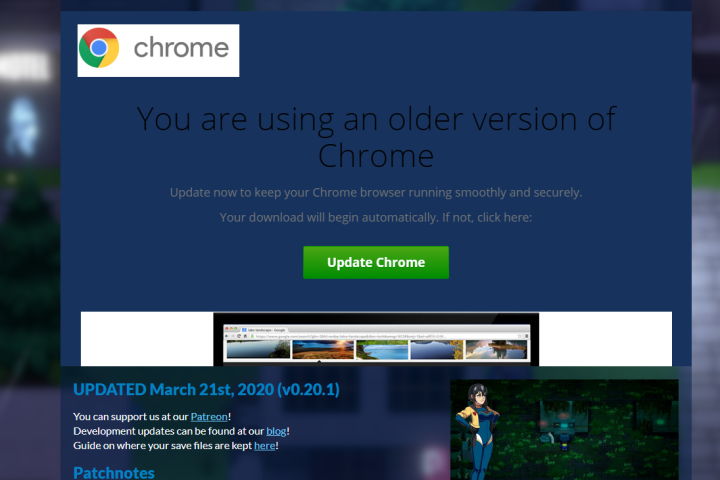
We've downloaded the webpage from this and it seems like the image of chrome in a screen at the bottom of the message is hosted on this domain: http://khmchamorshi.com/
The "Update Chrome" Button looks like this in html:
class="button eula-download-button download-button desktop-only hide-cros" href="blob:https://A_SUBDOMAIN_WAS_HERE.ssl.hwcdn.net/A_GUID_WAS_HERE" id="buttonDownload" download="Chrome.Update.41c9a6.js">Update Chrome
I replace a guid with "A_GUID_WAS_HERE" and a subdomain with "A_SUBDOMAIN_WAS_HERE" to make sure nobody clicks on this and gets a virus. Could it be that there's something wrong with itch.io's cdn?
Edit: I just checked the webgl.zip we uploaded by downloading it again from itch.io. The files are clean. It seems that the cdn is injecting this part of the website.

